Cyber Security Threats
As cost efficient as the use of automation technology is, it is often described as a ‘double-edged sword’, in that while it provides great benefits to Food and Beverage companies, it comes with an inherent risk and set of vulnerabilities.
With the introduction of specific modifications and upgrades to meet specific needs, over time a company may well find they are using a variety of equipment of varying vintages. The Food and Beverage industry’s slow realisation of the risks of cyber attack is in part due to this piecemeal approach to system modification, as bit by bit the processes become more automated and computer controlled.
Regulation has also been slow to catch up with the pace of automation. The FDA (U.S. Food and Drug Administration) does not currently consider cyber security to be part of food safety. Broadly, industry standards require securing all industry technology from cyberattack, but in the context of Food and Beverage this has not been addressed specifically. More emphasis, understandably, is placed on the danger to the consumer of contaminated products.
There is also a prevailing belief that the Food and Beverage sector is not in any significant danger of cyber attack as there is little financial gain to be made from doing so.
As a consequence of these factors (increasing automation, lack of regulation, and the belief that Food and Beverage is not a target of cybercrime), currently there is sense of complacency in regards to cyber attack in the Food and Beverage sector.
A security budget that focuses on doors, fences and other physical security measures is of no use if there is no consideration given to securing the sites information and automation technology. PLCs (Programmable Logic Controllers) are particularly vulnerable, in that they obey any command given to them regardless of the consequence and they are used extensively throughout all industries to interface between computers and automated machinery. In this new age of the ‘IIOT’ (Industrial Internet of Things) it takes more than a firewall and antivirus software to fully make a site cyber secure.
The risk to the Food and Beverage sector is unfortunately increasingly very real. In May 2017, the ransomware known as ‘Wannacry’ hit 200,000 companies across the world. The month after that ‘Petya’ infected more than 2000 companies and for the first time this included the Food and Beverage industry. Mondelez in the US and the Cadbury factor in Tasmania were both victims of the attack.
Being held to ransom is far from the only threat. Often, a cyber penetration is just the means by which another crime is attempted. This may include the theft of credit card details or any other form of data breach. Also, ‘Agroterrorism’, whereby hackers attempt to irradiate or contaminate food by gaining control of the automated equipment, is an increasing threat as systems become more complex. If an employee can link in from home, then so can anyone, and the convenience of being able to control a system from anywhere must be balanced against security concerns.
ANX Corp (now OpenText) identified the following security gaps that affect food and beverage companies: outdated firewalls, insecure remote access, weak security configurations, operating system flaws, lack of staff training, flawed security policies, negligence, and poor change control procedures.
In reality the Food and Beverage sector is the most targeted for cyber security attacks after Retail. According to Trustware Global Security, just under half of all attacks are against Retail and about a quarter are against Food and Beverage. It is worth noting that for many larger companies their business may cross both sectors with systems and technology being interlinked between the two.
The threat of cyber attack is not just limited to the big players. For instance, a family run bakers may have a secure database for distribution of its product, but how is customer financial information handled? A single attack on a small business can have devastating consequences.
For all businesses the loss of client confidence, the cost of stoppages and the spoilage of product can all result from a cyber attack and if the attack results in harm being done to consumers by tainted products then the damage done to the company will be greatly magnified.
Cyber Security Defence
There is little in the way of regulation specifically aimed at Cyber Security in existing Food and Beverage industry standards. The US Food Defence Plan is an overall methodology for Disaster Recovery and the FDA’s Food Safety Modernization Act (FSMA) requires adherence to stringent safety standards, but does not cover Cyber Security specifically.
Meanwhile, in the UK, the PAS96:2014 Guide to Protecting & Defending Food & Drink from Deliberate Attack deals primarily with the physical threats of interference to food and beverage. It does however list ‘Cyber Crime’ as a form of attack.
In terms of global regulation there is TACCP (Threat Assessment Critical Control Point) developed in reaction to the increase in food fraud. TACCP builds on the older HACCP, (Hazard Analysis Critical Control Point) originally developed in the 60’s to control the food given to astronauts and now used industry wide to prevent food poisoning.
IEC-62443, while not specifically dealing with Food and Beverage, is the industry wide cyber security standard specific to automation. It recommends the development and use of a CSMS (Cyber Security Management System). In the same way that a mixer or palletiser is maintained through a HACCP program, the information and control technology should be maintained and monitored by a CSMS.
Maintaining backups, keeping systems up to date, change control, employee training, and the segregation of networks should all be managed by a CSMS in order for it to be effective. It is clearly sensible to plan for an attack before it occurs and this should be done as part of the company’s overall Disaster Recovery procedure, which is covered next.
Disaster Recovery
Disaster Recovery is a subset of an overall Business Continuity Plan. Primarily it is the management of data such that it is recoverable in the event of a disaster. Statistically businesses are likely to fail in the years following a major disaster and this becomes a virtual certainty if no Disaster Recovery Plan is in place. This is why the majority of large organisations already have such plans defined as part of their standard operations.
While automation and computer systems are vulnerable to the same things that all other equipment are, such as fires and floods, they are also vulnerable to the intangible threat of cyber attack.
To counter this threat, at the very least, backing-up operating systems and data is vital. How this digital information is processed, stored and retrieved should be laid out in the Disaster Recovery Plan. In most cases it is not simply enough to take backups and put them on a network drive somewhere, thought must be given to how software patches are handled, how older versions are stored, how safe the stored information itself is from attack, and the process by which the stored data is to be restored in the event that it is required.
The Plan should also consider that most systems are constantly changing. Change Management processes should account for the taking and storing of backups and ideally be fully integrated into a controlled process. Research shows that a more encompassing, holistic, approach to disaster recovery planning saves money, time and reputation in the event that it is required.
After a major incident, even with a plan in place, there is a moderate chance the affected company will never recover. Without Business Continuity and Disaster Recovery plans this becomes a near certainty.
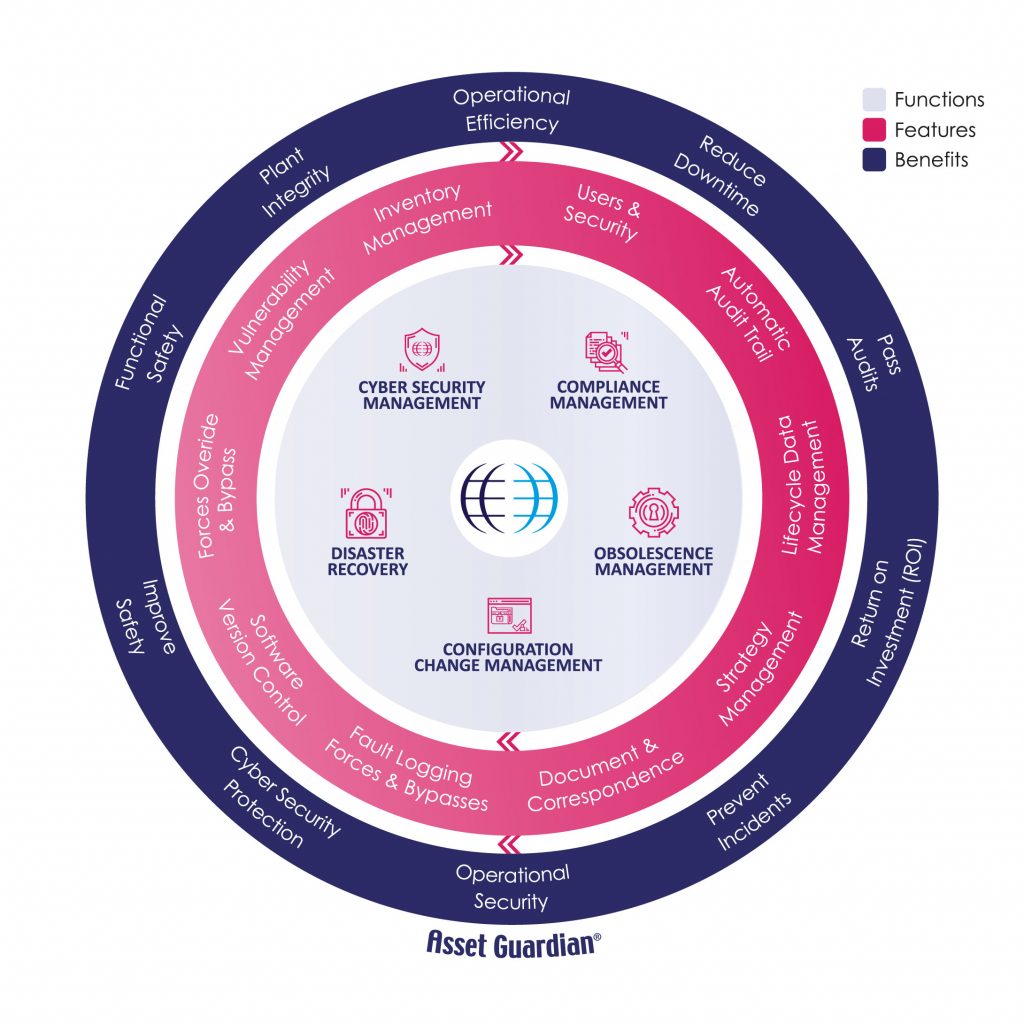
Asset Guardian’s role in Cyber Security and Disaster Recovery
Asset Guardian offers a solid foundation for Cyber Security and Disaster Recovery in the Food and Beverage sector.
Asset Guardian can act as the central point of a CSMS (Cyber Security Management System). A CSMS is the documents, processes, procedures and systems that form a company’s Cyber Security effort (as defined in industry standard IEC-62443).
As part of the CSMS, Asset Guardian also provides the facility to:
- Identify risks
- Organize user training
- Implement business continuity and disaster recovery plans
- Organize and structure personnel, physical and environmental security
- Document network segmentation
- Record Access Control (i.e. Administration/Authentication/Authorization)
- Improve Incident Response
- Provide Analytics to improve, develop and maintain the overall CSMS
Asset Guardian’s primary purpose is to act as a secure location for the backup of control system software and as such offers a sound platform for a fully integrated Disaster Recovery Plan.
Disaster Recovery Features include:
- Secure Software Storage
- Version Control
- Process Software Configuration Management
- Change and Obsolescence Management
- Auditing and Validation
- Regulatory Compliance
Written by Graham Foss. As one of AGSL’s team of Technical Consultants, Graham Foss is responsible for implementing the company’s product development and technology strategy. Before joining AGSL in 2016, Graham was employed for 12 years as a lead software engineer at Aker Solutions Subsea Ltd, where he worked on projects in the North Sea, North Atlantic and Norway. Graham holds a degree in Computing from Edinburgh’s Napier University in Edinburgh, where he graduated with distinction. A Chartered Engineer, he is a member of the Institution ofEngineering and Technology (IET).