The OT cyber threat intelligence gap is real therefore it is no secret that cyber attackers target, and have a robust understanding of Operational Technology (OT) and the Industrial Control Systems (ICS) environment.
In an alarming study, Gartner predicts that by 2025, Cyber Attackers will have such targeted control over Operational Technology environments, that it will successfully harm or kill humans.
Why is there a greater need for improved OT Cyber Threat Intelligence?
Operational Technology refers to both hardware and software that monitors and controls industrial equipment, processes and assets. Whereas IT systems manage data, OT devices control the physical world. As a result, OT systems remain a lucrative target for Cyber Criminals if the final result includes the shutdown of critical infrastructure.
This is why there is a greater demand for improved cyber threat intelligence across industries, so that operators can thwart cyber threats to OT systems.
Implementing an effective Cyber Security Management System (CSMS) has never been more important as it is the first step in securing ICS environments. With the Asset Guardian solution, compliance with cyber standards such as IEC 62443, NIST and other Industry requirements can be met.
You can expect to minimise cyber security threats, improve incident response rates, reduce or prevent downtime, and align your business needs to meet the required industry standards.
The Cyber Threat Intelligence Survey
A recent SANS Survey revealed gaps in perception around ICS risks at various levels within the organisation. A worrying 61% of respondents identified this and 35% indicating a gap between senior management and OT/ICS cybersecurity front-line teams.
Ransomware remains to be the biggest threat to operational technology (OT) systems and this is due to ICS operations leading to higher and quicker pay-outs.
It is critical that managers and leaders responsible for their OT/ICS assets, embrace the differences between IT/OT systems and support teams to create strategies to mitigate cyber risk.
The Impact of ransomware attacks across Industries

It is more imperative than ever that OT decision-makers improve cyber threat intelligence and seek OT security solutions to scale-up and apply across all of their OT assets. In the 2022 digitized world where operators are enduring their Industry 4.0 journey, devices are more connected, but vulnerabilities are increasing as a result.
Colonial Pipeline Ransomware Attack: Oil and Gas Industry
One of the more disruptive cybersecurity incidents that impacted OT systems took place in May, 2021. The attack, carried out by DarkSide, forced the shutdown of the Georgia-based Colonial Pipeline in the United States. Downtime lasted 6 days, and the main cause of attack was ransomware.
It occurred due to lack of visibility into the security status of the operator’s OT systems. It caused long periods of downtime, 100 gigabytes of data stolen, and $4.4 million paid to the hackers. The attack was the largest experienced on an oil infrastructure within the USA.
Toyota Ransomware Attack: Manufacturing Industry
Toyota is the world’s largest car manufacturer, and in February 2022, one of its suppliers – Kojima Industries, fell victim to cyber-attack. It took place within the computer server and disrupted the supplier’s parts supply management system. It resulted in the shut-down of 28 lines and 14 plants.
With over 10.5 million vehicles being sold in 2021, disruption to any part of the operator’s production line will result in monumental loss of profit. It took several days for the production to restart.
A Feature Rich Cyber Security Management System: Asset Guardian
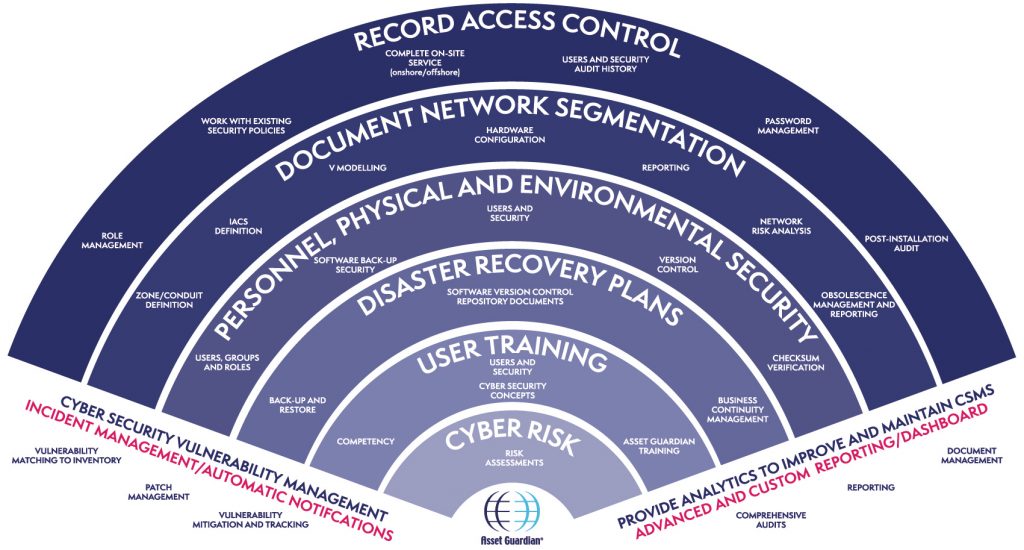
Operators require a set of systems and processes called a Cyber Security Management System. A CSMS allows you to develop a deep understanding of the threats facing Industrial Control Systems (ICS). By having an effective CSMS in place, you can achieve compliance to IEC 62443 and other essential cyber regulations.
The CSMS forms the core of an overall cybersecurity plan. An Asset Guardian CSMS would reduce risks significantly, and improve operations.
There are several layers to a cybersecurity management system, including elements, element groups and categories. It allows you to structure and manage cyber security activities in accordance with objectives and goals.
A Phased Approach to Cybersecurity Management Compliance

Asset Guardian employs a phased approach for operators to follow to achieve compliance with IEC 62243. The phased approach comprises of: Audit and Assess, Stabilise and Secure, Manage and Maintain, and Review and Revise.
Asset Guardian ensures that after each phase is complete, its findings and resolutions feed into the next stage until the process is complete.
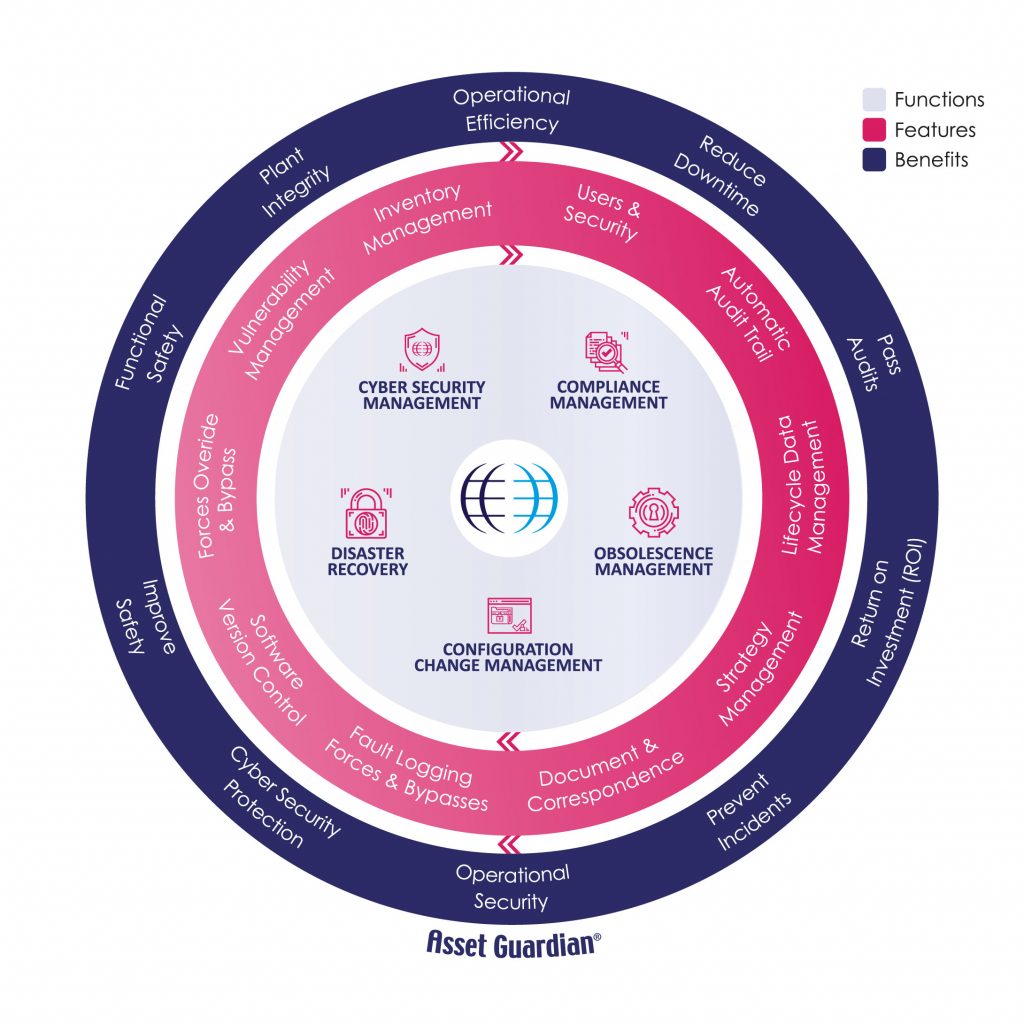
To ensure the CSMS is kept up to date, a system of Change Management is required to monitor any changes to your ICS environment. This also takes Obsolescence Management into account as it is a key issue in all ICS systems. Cyber risks will therefore feed into Obsolescence Management when creating strategies that include upgrades, patches and repairs. Disaster Recovery plans should also form part of your overall CSMS in the event of data loss or corruption.
Asset Guardian provides all features required as part of a CSMS including Configuration, Compliance, Obsolescence Management and Disaster Recovery. The diagram below includes the functions, features and benefits of the Asset Guardian solution.
What benefits can I expect from implementing an Asset Guardian CSMS?
Operators can expect a multifaceted solution that manages and protects process critical software. It is used extensively through Industries, and as part of an enterprise system for many global operators. By investing in Asset Guardian, you can expect to:
- Reduce or avoid downtime from ransomware attempts.
- Comply with Industry Standards, guidelines and regulations including IEC 62243, NIST Cyber Security Framework, NIS Directive, OG86 and CIC CSC.
- Protect your entire ICS assets and environment.
- Achieve operational efficiency, deliver risk reduction and improve safety.
- Suitable across any industry, including oil and gas, chemical processing and renewable energy.
- Work with front line monitoring tools.
- Achieve ROI.
If you are looking to implement a Cyber Security Management System, and would like to enquire about an Asset Guardian live demo, please get in touch today.
Written by Tina Campbell. Tina is the Marketing Manager for Asset Guardian Solutions Ltd. Tina is responsible for creating and executing the AG marketing strategy, and within that, developing and executing campaigns, creating and implementing content, managing website, traffic and social engagement and much more.