There are constantly new opportunities for cybercriminals and other cyber security threat actors to target Operational Technology (OT). The increase in cyber security threats is largely down to the move to homeworking, the array, and a vast quantity of new smart devices accessed by almost everyone across the globe.
As the digital footprint of organizations grows, so does the attack surface area available to cyber threat actors. Cyber-attacks are becoming more sophisticated, reaching into the online cloud and the supply chain in search of exploitable vulnerabilities.
Additionally, the fact that the cybersecurity industry currently has a critical shortage of trained professionals means that cyber-attacks are increasing in volume and scale.
Top Cyber Security Threats to Operational Technology
From relatively small-scale attacks that target individuals for personal gain to nation-states attempting to cripple the critical national infrastructure of their enemies, there has never been a more crucial time to anticipate and understand the developing threats and trends in the Cyber Security industry.
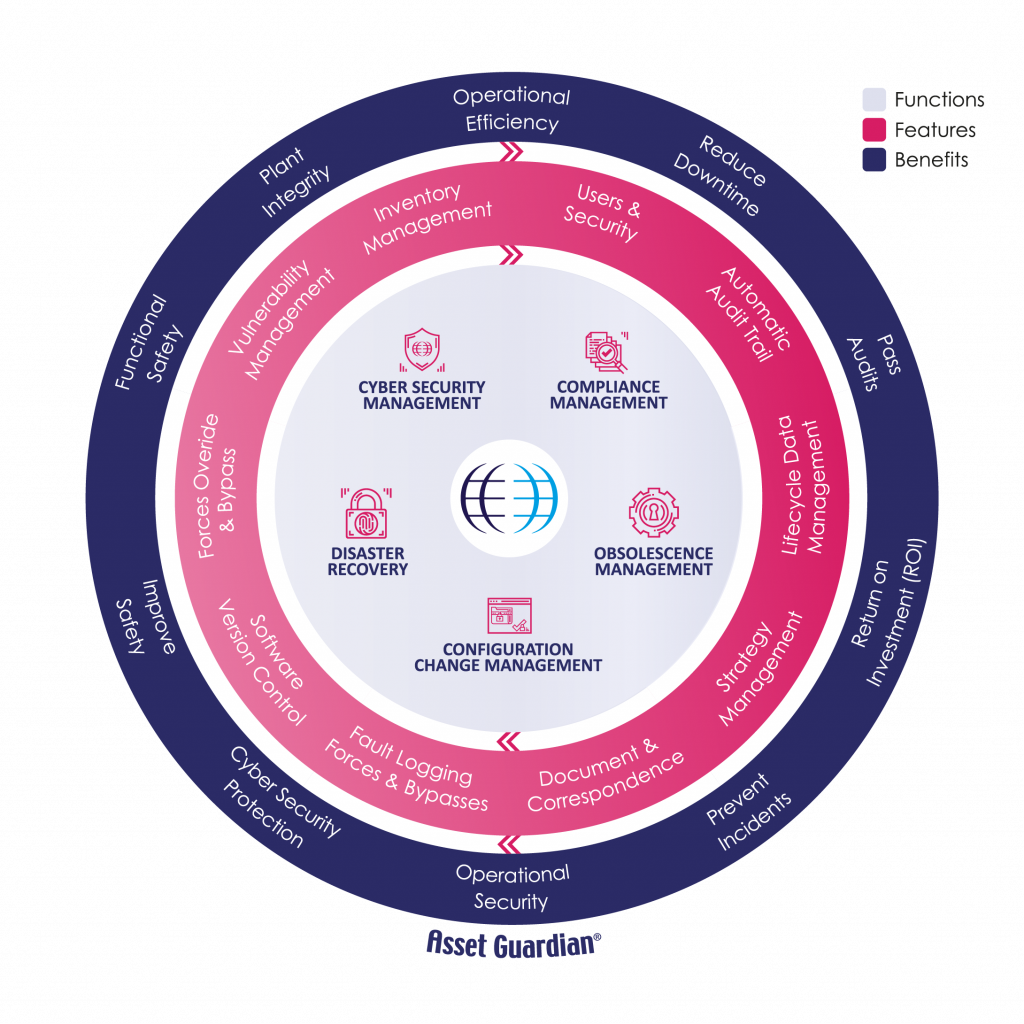
The Asset Guardian Solution
Cyber Security threat actors are becoming more audacious, no longer lurking in the shadows, and are capable of attacks on a scale that can have an impact on nations and entire industries.
The increase in targets, such as a cloud-based workforce and the volume of smart devices now available, has led to a corresponding increase in cyber criminals and other cyber threat actors. Consequently, organisations will face increasingly sophisticated, insidious, and damaging forms of attack.
The Key to defending against these modern and evolving threats and the increase in vulnerable assets is the development and implementation of a CSMS (Cyber Security Management System).
Asset Guardian has been designed to form the backbone of a robust, integrated, and user-friendly Cyber Security Management System and is compliant with IEC-62443 and other Industry Standards.
As part of the CSMS, Asset Guardian also provides the facility to:
- Identify Cyber risk
- Organise user training
- Implement business continuity and Disaster Recovery plans
- Organise and structure personnel, physical and environmental security
- Record Access Control (i.e Administration,/Authentication/Authorisation)
- Improve Incident response
- Provide analytics to improve, develop and maintain the overall CSMS.
Asset Guardian used as a Cyber Security Management System minimises cyber security threats, greatly improves incident response and aligns your business to the IEC 62443 Cyber Security Industry Standard.
Increasing and Evolving Cyber Attacks
All forms of cyber-attack are on the increase, in particular Ransomware attacks. Global Industries targeted include healthcare, education, finance, and national infrastructure.
Cybercriminals and other threat actors continue to improve and modify their techniques. Every new development in the world of technology is examined for its potential to be a new attack vector or as a way of making an existing form of attack easier or more rewarding for the attacker.
Ransomware attacks, a form of malware that threatens to publish, block or delete the victim’s data unless a ransom is paid, are on the increase. Ransomware became commonly known outside of the tech industry after the Wannacry attacks of 2017. Subsequent high-profile attacks have ensured that Ransomware remains one of the highest risks to organisations across the world.

In addition, the advent of cryptocurrencies like Bitcoin means that ransoms can be paid anonymously by the victim. This potentially saves their reputation but increases the likelihood of further attacks.
And even after paying the ransom, stolen data may still be released or sold anyway, meaning that ultimately the victim loses both their money and their reputation.
During the pandemic, some organizations temporarily relaxed their firewall and security protocols to enable staff to work from home during the lockdown. While security measures have been and continue to be introduced, this has not been as swift as it could have been, and gaps remain that threat actors continue to exploit.
Ransomware as a Service (Raas)
Another alarming new threat is the concept of ransomware as a service (RaaS). RaaS is a software-as-a-service attack vector, part of the emerging cybercrime gig economy, that sells ransomware to criminals with no coding knowledge.
All these factors ensure that ransomware attacks are still a very serious threat, that will continue to increase while it is effective and profitable.
Ransomware is far from the only form of cyber-attack on the increase though. Malware, Distributed denial of service (DDoS), Password attacks, and Man-in-the-middle attack (MitM) are just a few examples of the increasingly large toolkit of attack vectors available to cyber criminals.
Cloud-based Services and Infrastructure
With the tectonic shift to working from home since the global pandemic, there has been an increase in cloud-based services and infrastructure.
Solutions have been rapidly put in place to meet this unprecedented demand and to allow the new remote workforce easy access to cloud-based solutions such as file sharing, online meeting places, and other collaborative working tools.
This is a massive change in working practices and it has not gone unnoticed by cyber security threat actors. A recent example is the Russian ‘Cozy Bear’ abuse of Azure to hack into Microsoft 365.
Cybercrime is not the only consideration when it comes to managing data and resources in the cloud. As the amount of available space for data increases, its management becomes more difficult.
Data lakes, data that is stored in a natural or raw format, when unmanaged can turn into data swamps or eventually data graveyards and pose long-term security risks.
Software Supply Chain
Cyber-attacks on the software supply chains of organizations are on the increase worldwide. The software supply chain can broadly be described as the components, tools, and processes that take software from early development to end users.
Software tools may become compromised, or third-party development software may contain vulnerabilities. Supply chain cyber-attacks cause a great deal of business disruption and are increasing in threat and damage caused to OT.
The 2020 SolarWinds supply chain attack is a good example, where vulnerabilities in Microsoft and VMware software enabled Russian hackers access to emails and sensitive documentation.
More recently the Log4j zero-day vulnerability, unnoticed since 2013, enabled cyber security threat actors to run Java code on the victim’s servers, opening the door for all sorts of other mischiefs such as ransomware attacks and botnets.
Reliance on Third Party Vendors
Most organisations consider cyber security a primary concern when choosing third-party vendors, and yet many do not have dedicated personnel tasked to manage these vendors and employees.
Recent studies have shown that over half of data breaches have involved a third-party organisation, with data being lost or stolen in transit, or because of vulnerabilities in commercial software.
The good news is that tighter regulations make it easier to select vendors based on their adherence to globally accepted standards. In addition, many security product vendors are merging functions into more affordable solutions as part of an integrated suite of tools.
Mobile Devices
Many day-to-day activities have moved to mobile devices, for instance, there have been banks around for years now that exist purely as mobile phone applications. Healthcare too, from diagnosis and consultation to medical records is often mobile and accessible online.
Another consideration is the practice of ‘bring your own device’ (BYOD) another recent consequence of the shift to remote working.
Most organisations will now have security policies in place for the control and management of nomadic devices, but cyber security personnel can usually only control these devices when connected to their networks and domains. Unknown and unmanaged devices may contain viruses or malware and potentially have critical protections disabled.
Productivity must be balanced against security. Ease of access is important but should not run to the detriment of protection against all the threats that are being associated with connecting devices to the internet and each other.

Artificial Intelligence in Cyber Attacks
As we move more and more into a future where AI becomes part of the digital world, the increasing reliance on Artificial Intelligence and Machine Learning has not gone unnoticed by cyber security threat actors. Not only the exploitable vulnerabilities of this new architecture but also how it can be turned against the defenders as part of new or existing attack vectors.
At one time AI was in the realm of science fiction and developed only on supercomputers, but now there is enough processing power on a standard laptop and available tools to create methods of cyber-attack that use aspects of Artificial Intelligence to increase their efficacy.
State-Sponsored Cyber Attacks
On a larger scale, there is still an ongoing threat of attacks that target critical national infrastructures (CNI) such as transport networks, electrical grids, and water treatment plants. Other targets may be military servers and electoral data.
The new global politics of the 21st century, with rogue states and advanced cyber warfare techniques, has increased the likelihood of a state-sponsored attack on Western national interests and organizations. State-sponsored attacks can be expected to have large budgets and as their primary motive is not financial, they are focused on doing the maximum amount of damage to their victims.
As an example, Russian threat actors attacked Ukraine in 2017 with malware software called ‘Petya’ and ‘NotPetya’. The attack was on Ukrainian banks, government ministries, energy firms, and media organisations, but it also spread across the world. Petya was disguised as ransomware, when in fact its primary purpose was purely destructive.
As more infrastructure, national grids, and networks increase their connectivity, so too does the attack surface (available attack vectors) available to cyber threat actors.
Human Error and Social Engineering
Social engineering attacks are getting smarter. Confidence tricksters and con artists have been part of human society since the dawn of civilisation. Just as in times past, social engineering cyber-attacks work by manipulating users into handing over sensitive information or acting against their better judgment.
Most online users may think they are clever enough not to be taken in, but recent reports show that an alarmingly high percentage of people can still be fooled by simple email scams.
Social Engineering attacks include Phishing (attackers send illegitimate emails to gather sensitive information), Scareware (the attacker tricks the victim into acting against fake malware or illegal content), and Water Holing (infecting commonly visited websites with malware that are frequently visited by the victim).
There are many other forms of Social Engineering, and some are modern interpretations of age-old tricks, such as Vishing (voice phishing attacks) and Tailgating (simply following people into secure areas through gates and doors).
Human error is a common component of most breaches in data. It has become apparent that standard security awareness training, where the participants passively watch videos and presentations, is not enough.
Changes in behaviour (for example by using nudge techniques) and a security culture that takes a more holistic approach are being developed to enhance and compliment more standard training.
Looking for an OT Cybersecurity solution? Get in touch today.
Written by Graham Foss. As one of AGSL’s team of Technical Consultants, Graham Foss is responsible for implementing the company’s product development and technology strategy. Before joining AGSL in 2016, Graham was employed for 12 years as a lead software engineer at Aker Solutions Subsea Ltd, where he worked on projects in the North Sea, North Atlantic and Norway. Graham holds a degree in Computing from Edinburgh’s Napier University in Edinburgh, where he graduated with distinction. A Chartered Engineer, he is a member of the Institution ofEngineering and Technology (IET).